Am I being attacked?!
Recently there has been some new tools introduced in Microsoft Sentinel to help security teams understand better the types and methods of attacks they have faced, in addition to intelligence to help them perform proactive threat modeling to implement better defenses.
There has been very tight integration with the MITRE ATT&CK library which provides a knowledge base of adversary tactics and techniques based on real-world observations. Let’s explore the new tools.
Threat Analysis & Response Workbook
The first tool is a workbook that helps you understand the following:
- Lists the out-of-the box Microsoft Sentinel detections coverage across MITRE ATT&CK framework and the number of events coming for those detections.
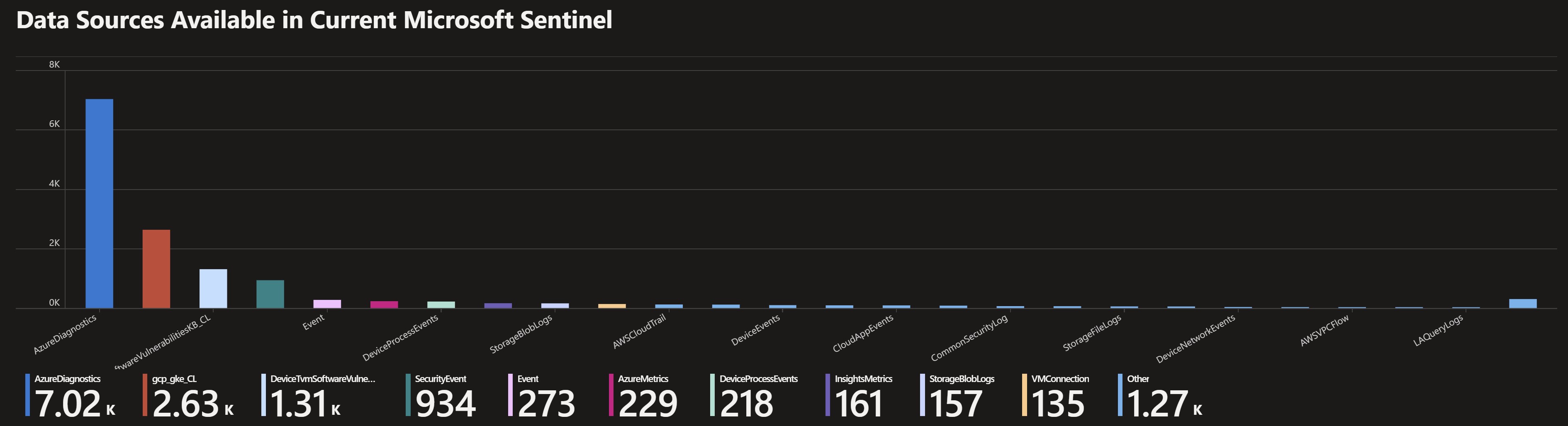
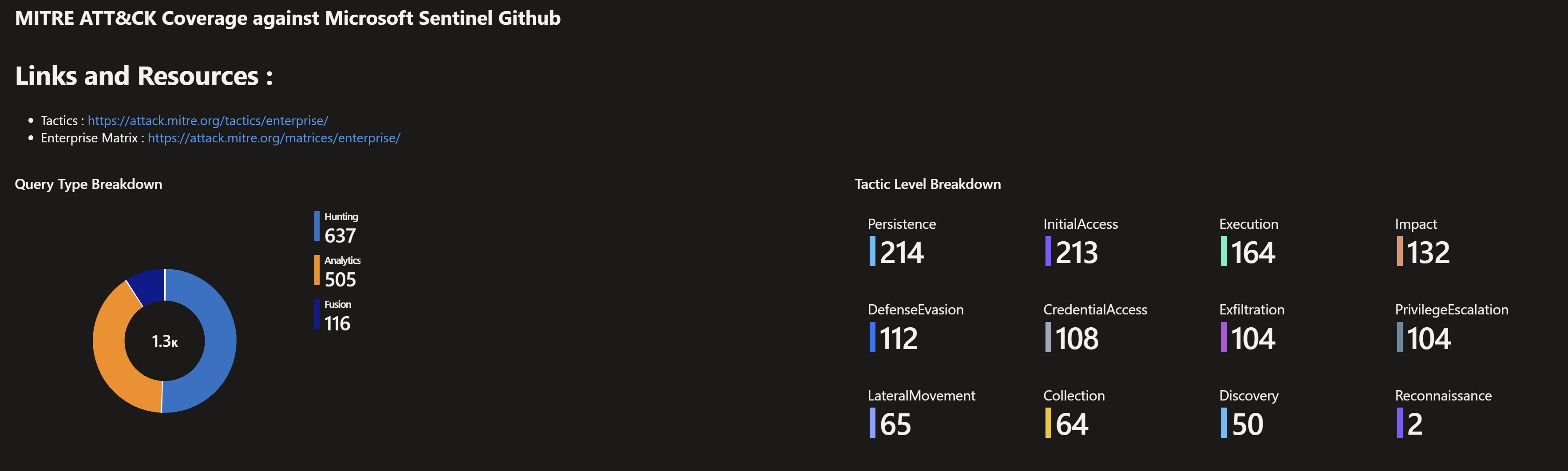
- Lists all of the Sentinel GitHub content categorized by detection type like hunting, analytics,..etc which is mapped to the corresponding MITRE tactics and also content by cloud platform, which helps understand for example what is avaialble for Azure Vs AWS Vs Office 365,…etc
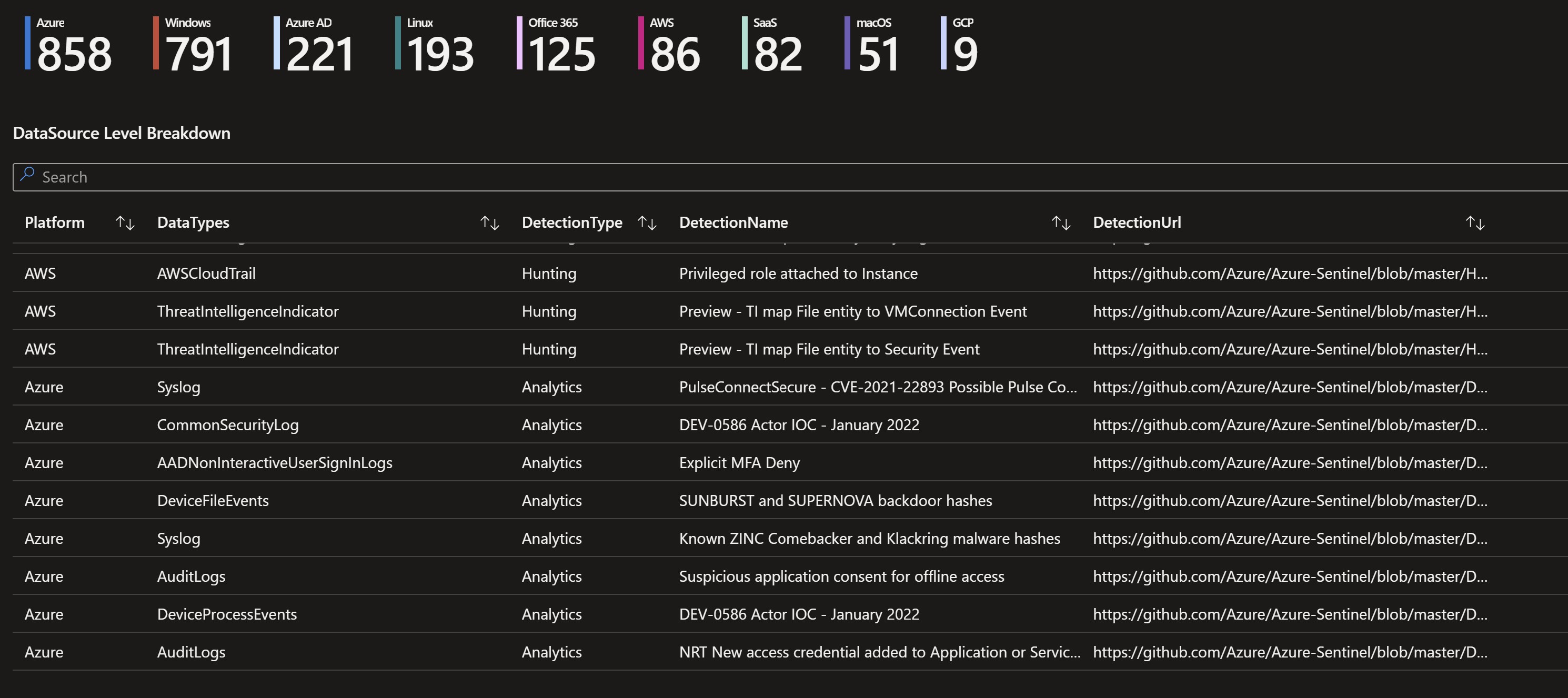
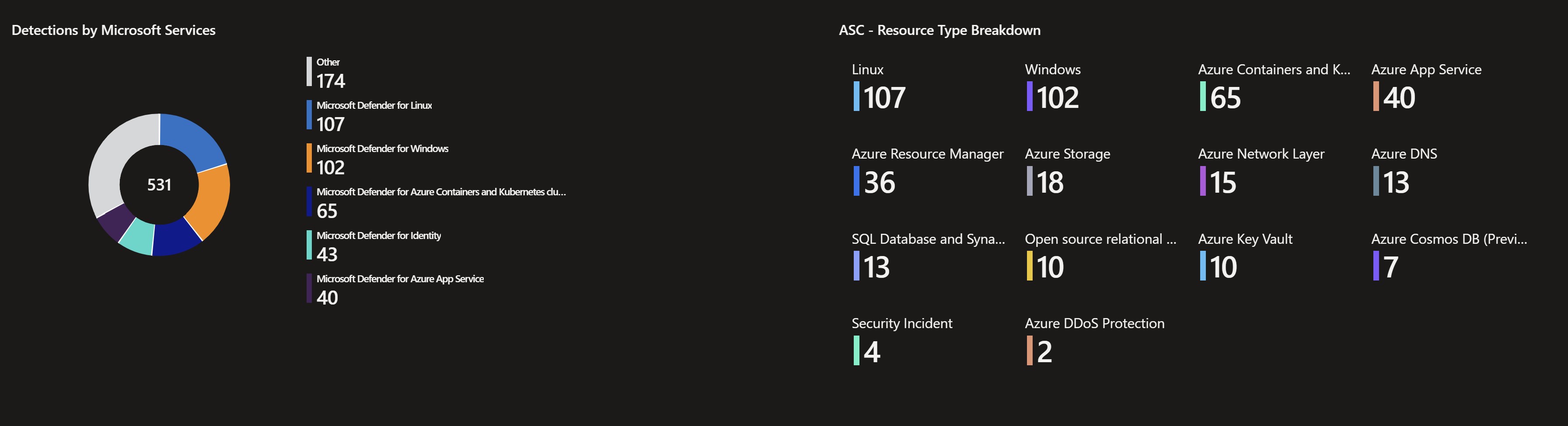
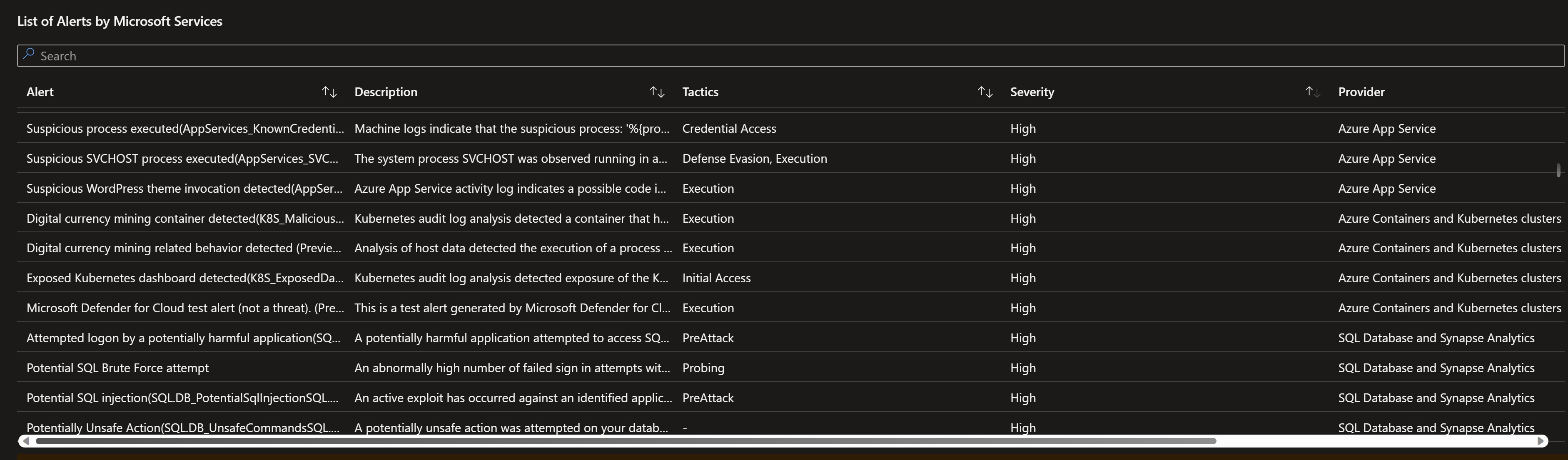
- Lists all of detections and alerts by Microsoft service so showing detections by Microsoft Defender for Linux, Microsoft Defender for Identity, Microsoft Defender for Containers ,…etc
- Shows a heatmap of all of the MITRE ATT&CK matrix categorized by cloud platform such as Azure, AWS, GCP as well as by service such as Azure AD, Office 365, Windows, Linux
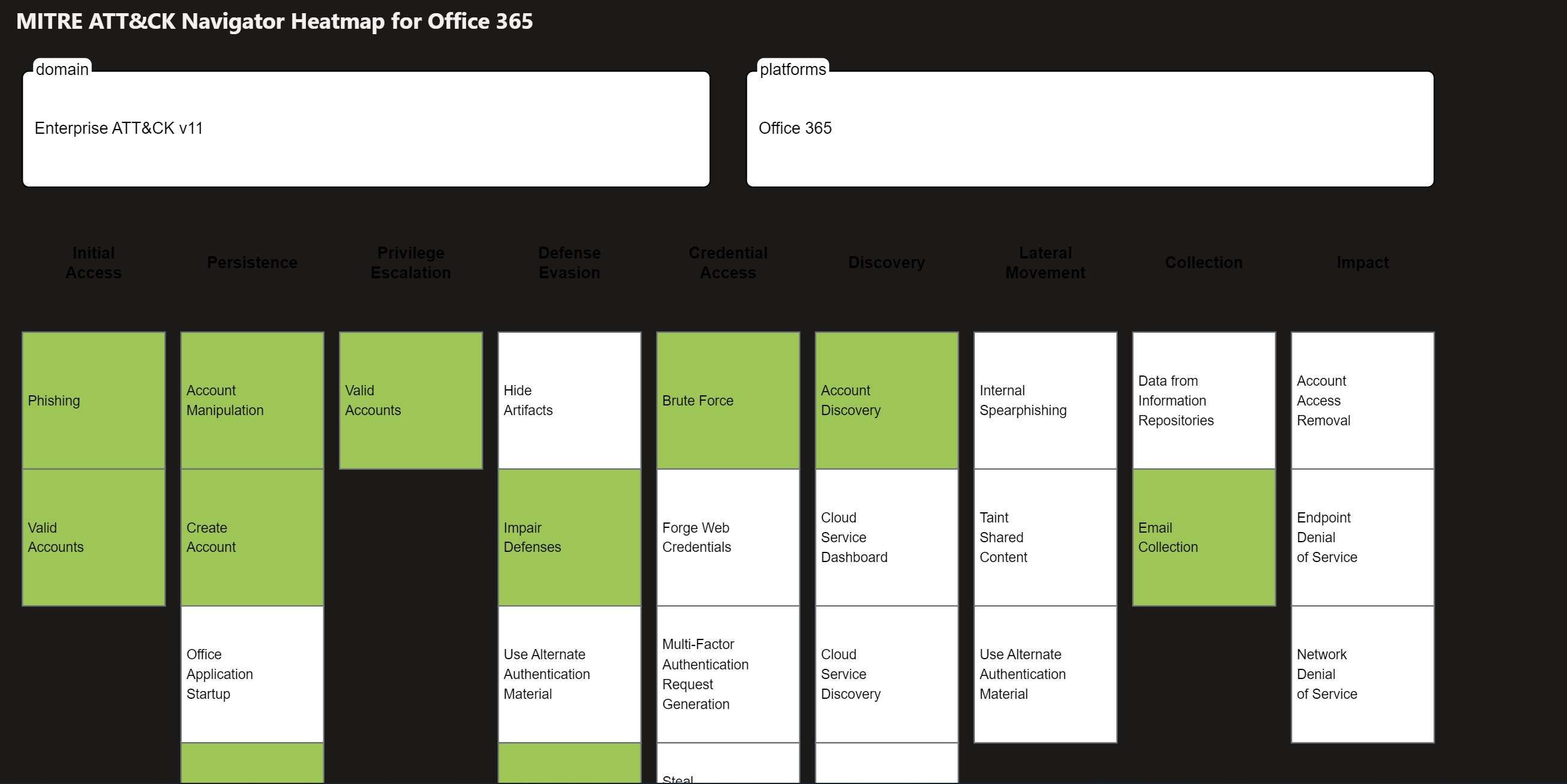
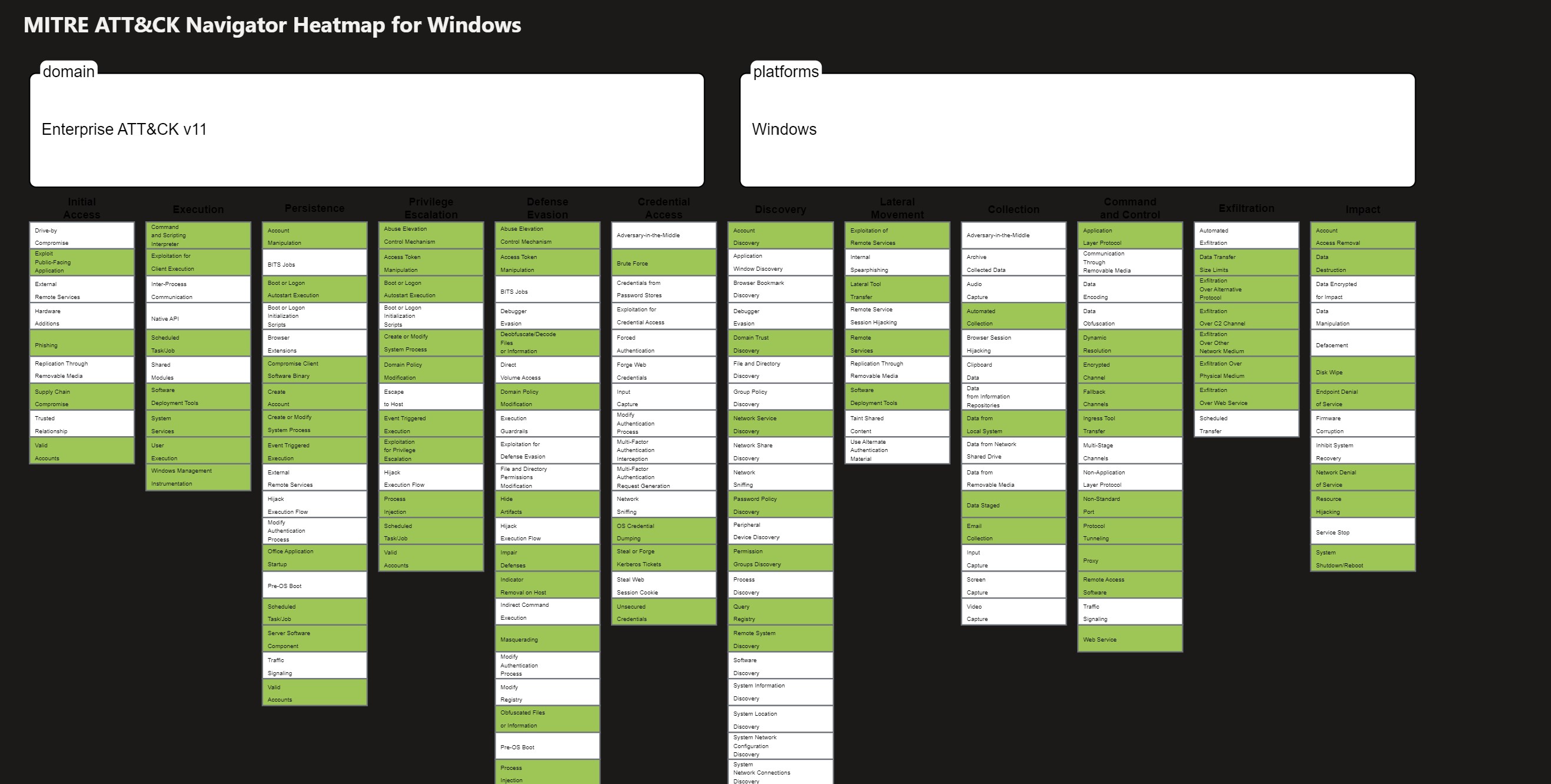
NOTE This workbook is mainly informational to help you understand your current posture and gaps.
Dynamic Threat Analysis & Response Workbook
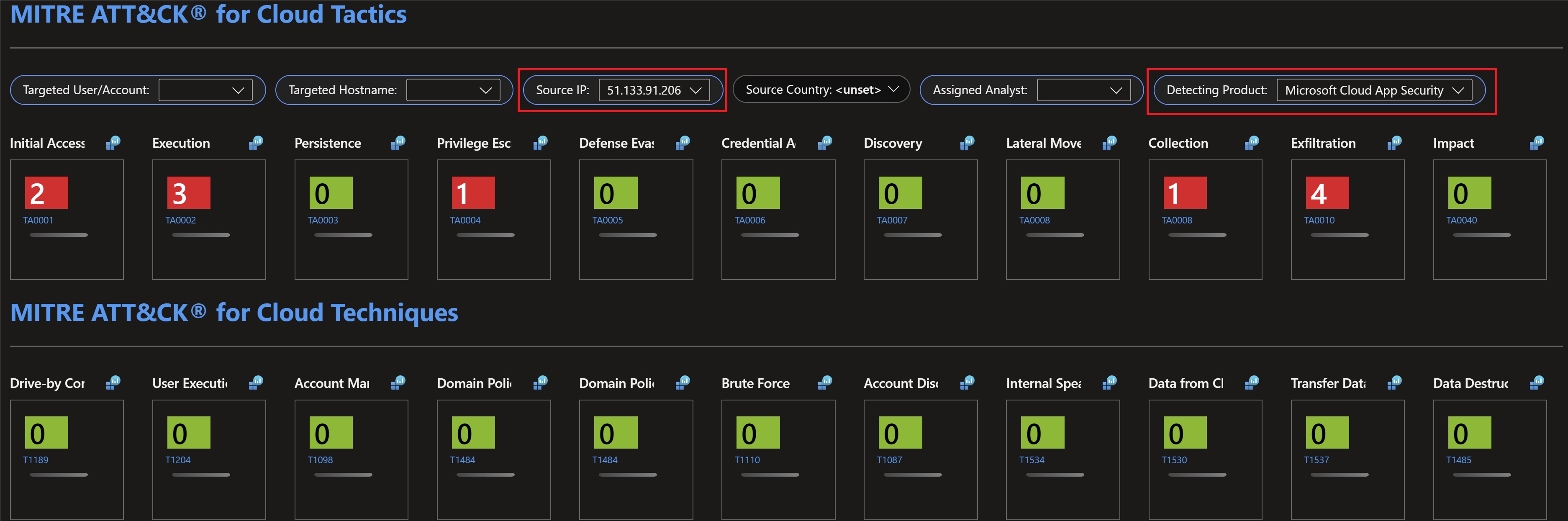
This workbook is actually pretty powerful, it visualizes all of the attacks to your cloud, onprem and multi-cloud resources and categorizes them to the corresponding MITRE ATT&CK tactic. This workbook allows you to perform hunting and investigation activities where you can focus on a specific user, source Ip address, country or machine.
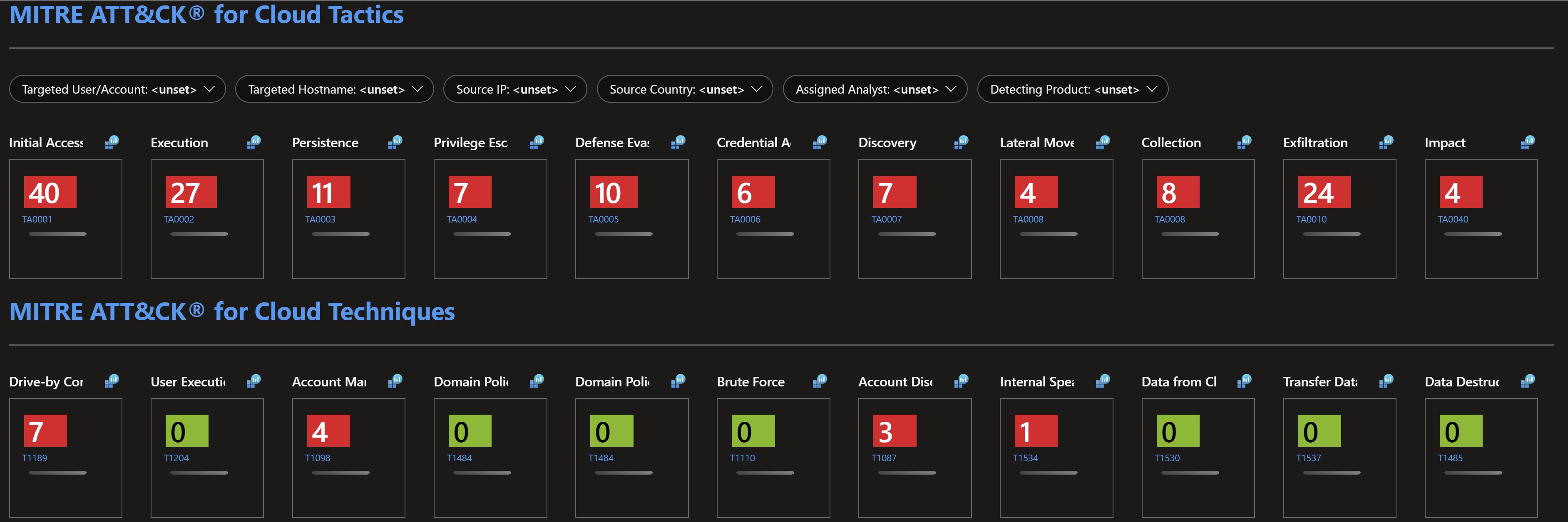
Filtering by a specific source Ip address and detecting product
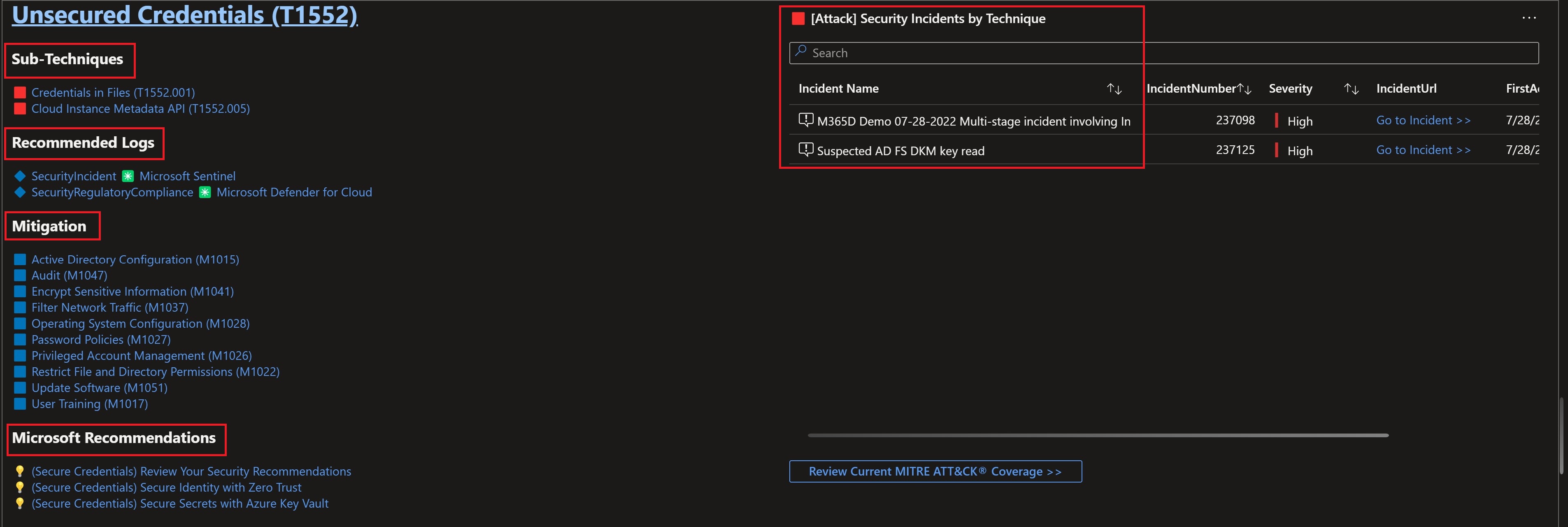
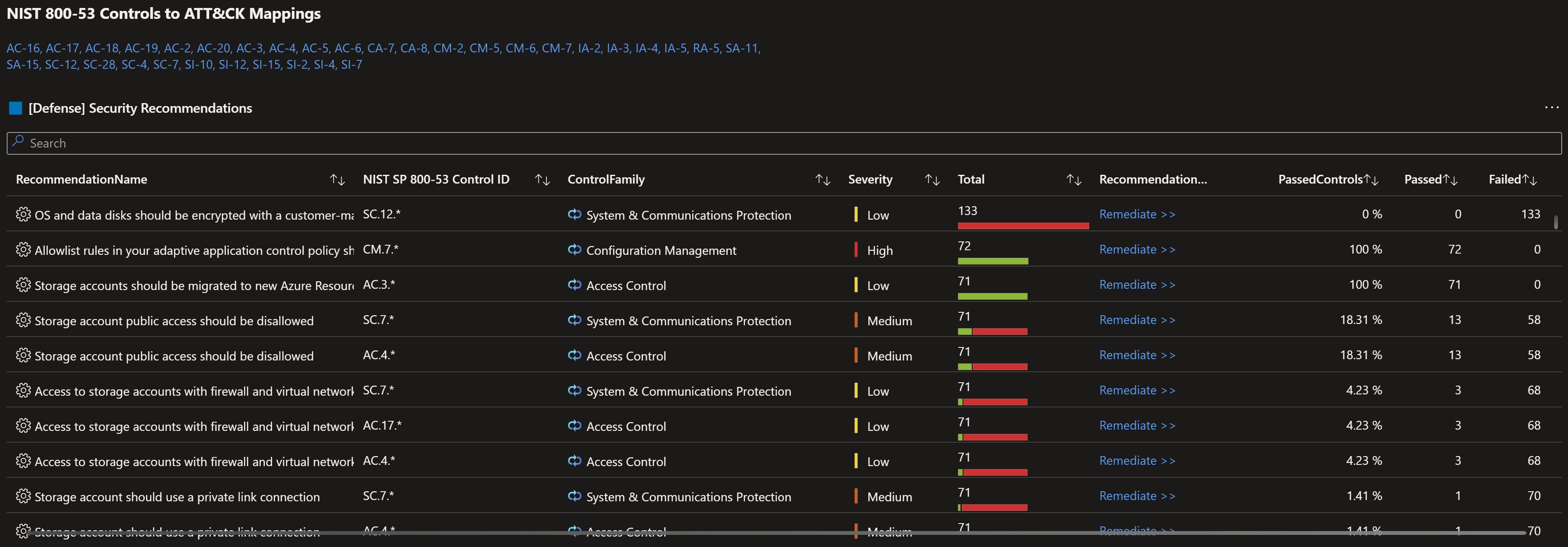
You get also useful logs to do more in-depth investigation, defense recommendations against those types of attacks, different resources to close those gaps in your environment and remediation through response playbooks.
MITRE ATT&CK Blade
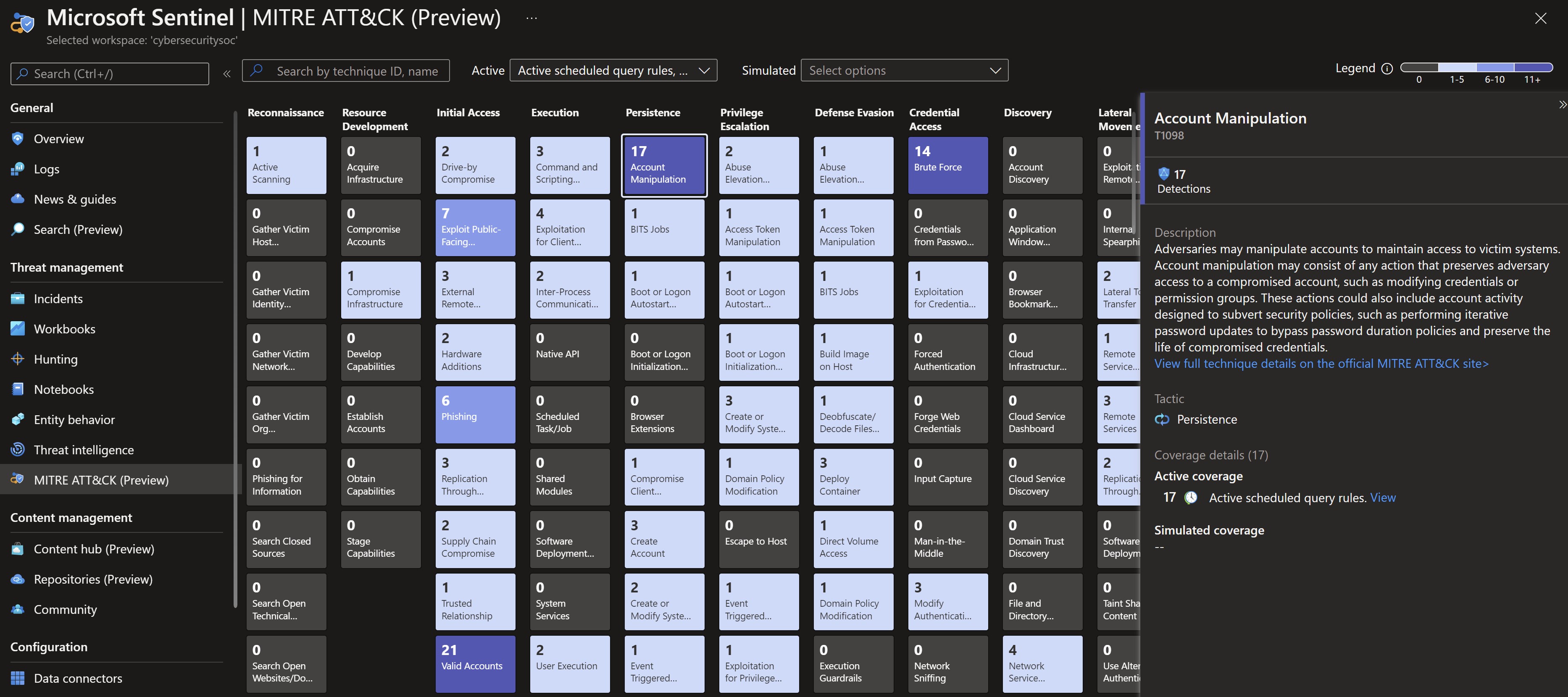
This is a new blade in Microsoft Sentinel that helps you to visualize your current coverage to understand if there are any blind spots or areas where you need to create your own analytics rules.
Workbooks deployment
To deploy those two workbooks you can either search for them in the content hub.
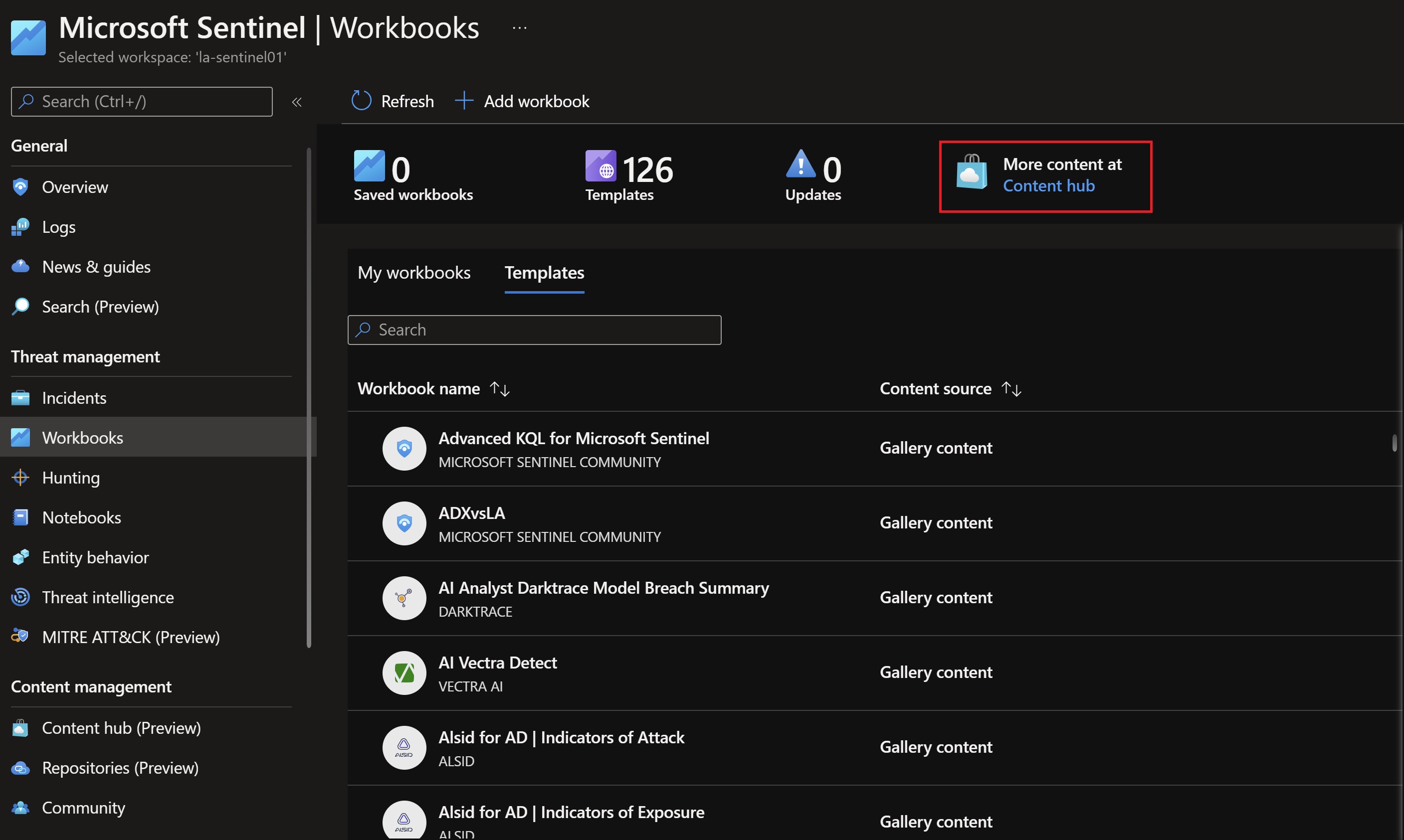
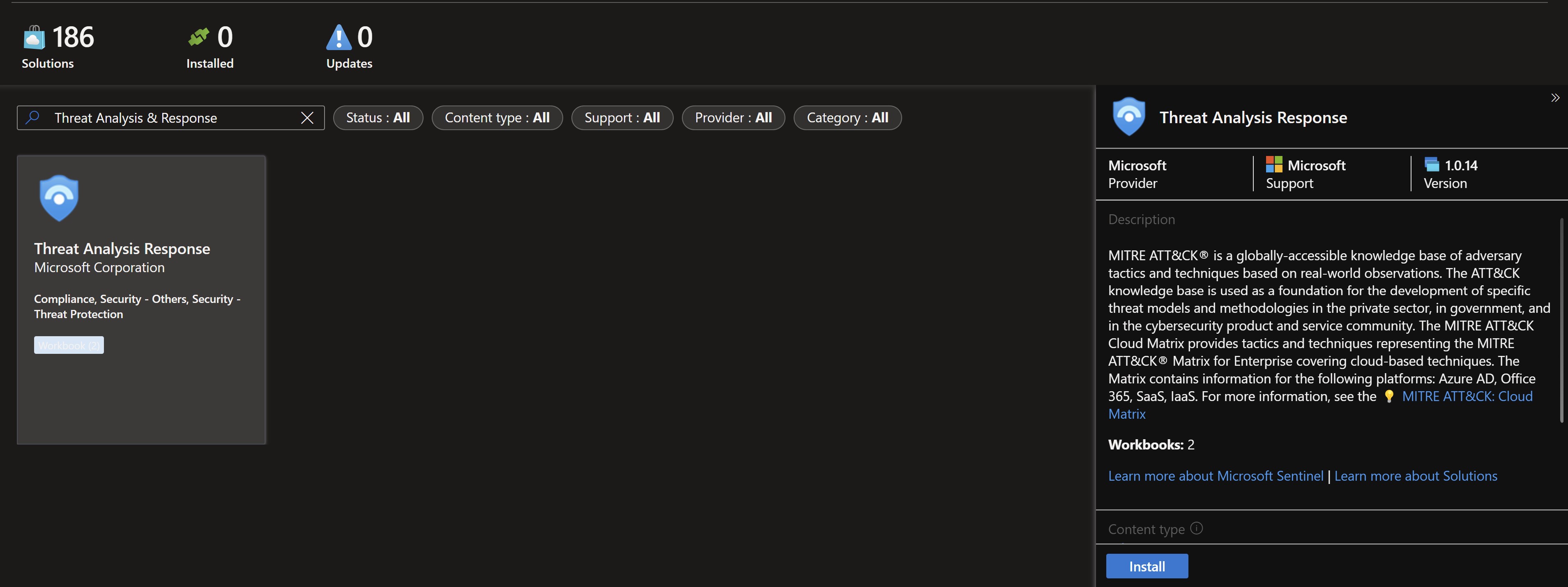
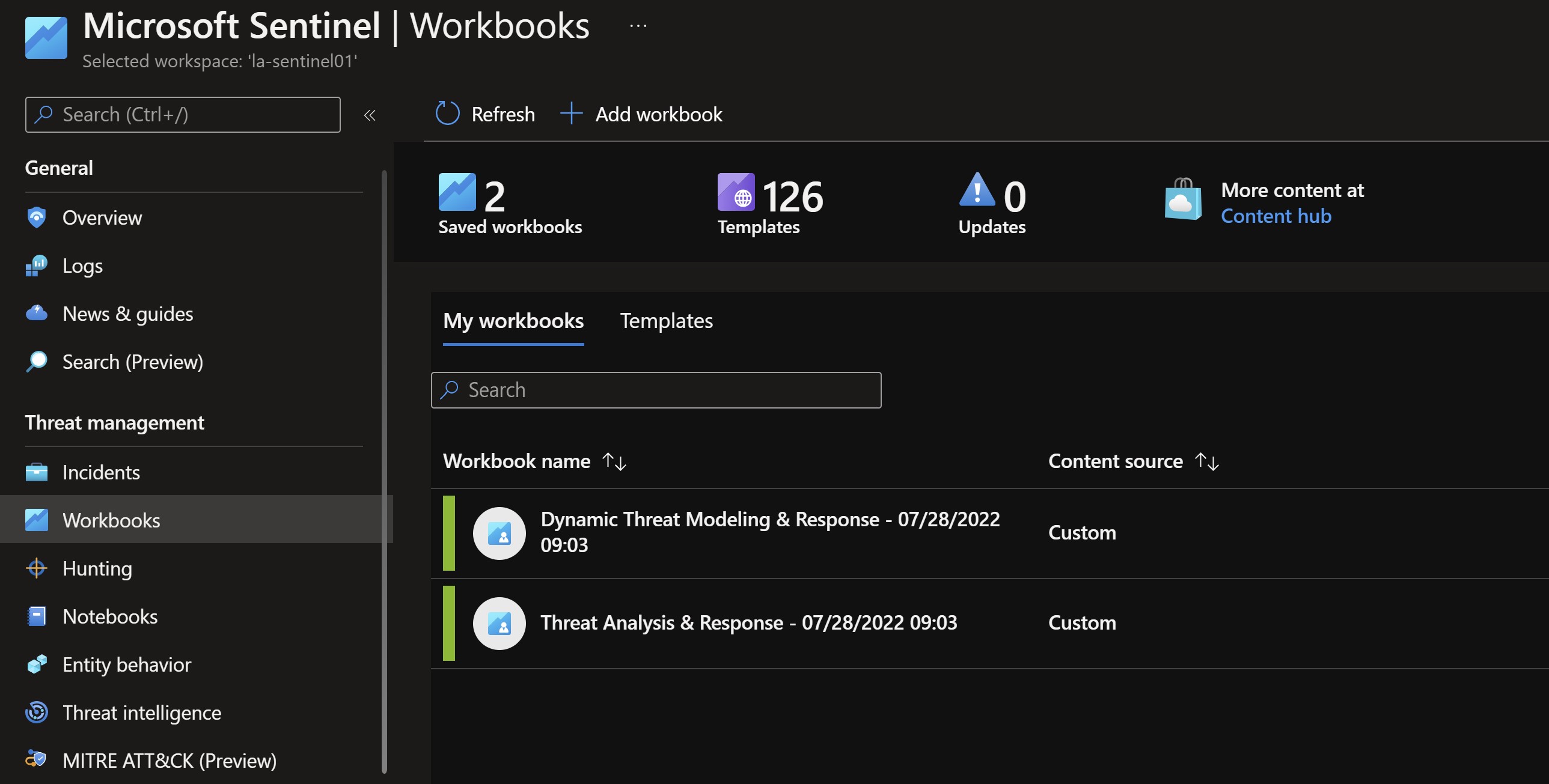
You can also simply deploy an ARM template which will install both workbooks into your Sentinel services
Video walkthrough
You May Also Like
Improving your security posture with Governance Rules
Microsoft Defender for Cloud analyzes your resources on a regular …
A better way to enable Azure Defender
Azure Defender is Azure’s cloud workload protection tool ,it …
Estimate your Infrastructure-as-code costs before deploying
I recently stumbled on a very useful API called Infracost, that allows …




